Dark endpoints: an invisible threat to your IT team

Invisible devices create significant blind spots that can leave IT departments helpless to act against a breach until it is already too late. A new report from Absolute found 13% of enterprise devices aren't connected to the corporate domain.
The Absolute platform delivers self-healing endpoint security and always-connected IT asset management to protect devices, data, applications and users — on and off the network.

The Invisible Threat: Building Cyber Resilience to Respond to the

Blog, Author, Michelle Base-Bursey

Cyber Security Glossary: The Ultimate List & Quiz

How Cybereason XDR Supports Zero Trust Initiatives

Proactive or Reactive Endpoint Security? A Critical Crossroads for SOC Analysts

Understanding Privilege Escalation and 5 Common Attack Techniques

Blog, Author, Michelle Base-Bursey

The Dark Web: How to Access and Potential Risks - CrowdStrike

How Lean Security Teams Can Overcome the Cybersecurity Spending

Julia Sustakova on LinkedIn: Dark endpoints: an invisible threat

Are You Familiar with the Monster in the Cloud?
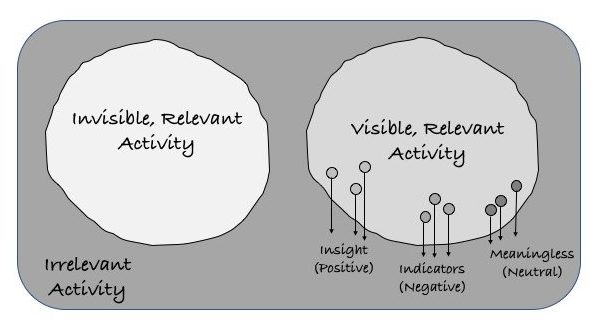
What Does Cyber Visibility Mean to You?

Endpoint Security Risks in your Organization and how to overcome

7 Lessons Every CISO Can Learn From the ANU Cyber Attack

How to Make Cybersecurity Effective and Invisible



/chantelle-soutien-gorge-sans-couture-absolute-invisible-c29260-noir.jpg)



